Although commercial software has played a large part in the IT boom of the past decade, an awful lot of that growth has been due to open source software. Indeed, without open source, the Internet itself would exist in a far different form, if it existed at all. Many of the technologies that helped build the 'net can be used to get us away from paying the "Microsoft Tax," at least in certain circumstances.
If we are going to come up with a viable replacement for Windows as an NOS, it will need to provide the same services as Windows, and preferably more, and at a better price point. At a minimum, we'll need a platform that can provide the following services:
- Windows file and print sharing, without having to add software to the clients
- POP and IMAP email retrieval
- SMTP for sending mail
- Web proxying and DNS
- DHCP services to minimize IP administration
- SQL databases
- Graphical administration tools (more on this below)
- Remote administration tools
- Better security than Windows NT/2000
Although many Linux/UNIX diehards disagree, many, if not most system administrators nowadays are more comfortable working with a GUI, and therefore more favorably disposed towards an OS with one. But a problem with GUIs is that when they are running, but not actually being used, they take up disk space and system resources. So the ideal OS might be one that offers a GUI, but doesn't make its use mandatory for administration: one that only runs when needed.
Such an OS doesn't appear to exist, but I found a way to satisfy these requirements by combining a couple of existing software packages.
The tendency with most NOSes is to activate all services by default. This makes it easier for the inexperienced admin to set up a server, but results in one that is wide open to attack. Since we're looking for a security improvement, I wanted an NOS which when installed activates a minimum of services automatically.
Specifically, I was looking for a Linux distribution that was designed somewhat along the lines of OpenBSD, i.e., "secure by default." Also, it should also give me flexibility as to partitioning and what software is installed.
I'll note here that OpenBSD would probably fill most of my requirements once we found a suitable GUI, but I'm more familiar with Linux, and so chose it for this project.
Several security-oriented Linux distributions have been introduced recently; EnGarde and the NSA's Security-Enhanced Linux come to mind. EnGarde even has a nice web-based GUI, but the installation process does not allow you to specify the partition structure. This put EnGarde out of the running, since specifying your partitions based on your available disk space and operating requirements is key to optimizing your server's performance. Partitioning can also have security implications. More info on EnGarde is available on their Web page, http://www.engardelinux.org/.
I also ruled out the NSA's Security-Enhanced Linux, as it still seems to be more of a research project, rather than a ready-for-primetime distro. From the SELinux FAQ:
"Security-enhanced Linux is a research prototype of the Linux(r) kernel and a number of utilities with enhanced security functionality designed simply to demonstrate the value of mandatory access controls to the Linux community and how such controls could be added to Linux. The Security-enhanced Linux kernel contains new architectural components originally developed to improve the security of the Flask operating system. These architectural components provide general support for the enforcement of many kinds of mandatory access control policies, including those based on the concepts of Type Enforcement(r), Role-based Access Control, and Multi-level Security."
More information on SELinux can be found at http://www.nsa.gov/selinux/.
With this in mind, I thought I'd give Trustix Secure Linux 1.2 a try. I downloaded the Trustix .ISO from http://www.linuxiso.org using my employer's OC3 line onto my laptop, then took it home and burned it onto a CD. Trustix's website is http://www.trustix.com.
Trustix 1.2 is a Linux distro based on Red Hat 6.x, but implemented in a security-conscious manner, and installs kernel 2.2.19-4tr. Only a bare minimum of services start up by default even when you install everything, as I did. The services enabled by default are:
- crond
- keytable
- netfs
- network
- postfix
- random
- syslog
That's a pretty bare system by anyone's standards. I even had to
enable sshd, which is included for remote admin, but
is not enabled by default. This was pretty easy by issuing the
command ntsysv at the prompt, then selecting
sshd.
Trustix also increase security by replacing insecure
applications with modern replacements. E.g., sendmail is replaced
with Postfix. Also, there is no telnet daemon (server) in Trustix;
as noted above, it's replaced with sshd. A telnet
client is installed, however, since it is useful for connecting to
those network devices, such as routers, which need it for remote
administration.
Incidentally, Trustix has some good documents on their website about installing and configuring the OS. The docs are also included in a variety of formats on the installation CD. One thing that I was pleased with is that although Trustix hails from Norway, the English language documents are well done.
Installation is done the old fashioned way, in character mode.
In fact, anyone who's installed an older version of Red Hat, or a
current version in text mode, will be looking at something quite
familiar. I chose to install everything, to get a feel for a full
install. This took up about 485 megs or so on my disk. Compared
with most recent Linux distros, this is quite lean. Installation
took about 10-15 minutes on a P-III/450 with 256 megs of RAM, a 32x
CD-ROM drive, and a 10.2 gig Maxtor ATA-66 hard disk. This included
the time to set up my partitions using Disk Druid. You can use
fdisk to partition your disk, by the way, but I find
Disk Druid easier to use.
One thing Trustix does not include is XFree86: in other words no graphical user interface. The authors of Trustix are avowed command line fans and feel that a GUI doesn't belong on a server, sucking up resources and introducing potential security holes. Instead, they intend for it to be administered from the command line.
While the "no GUI for servers" school of thought has its merits, I like having a GUI available for administration tasks. Even though I've been using Linux for a few years, and I can get around on the command line without problems, having a GUI helps me keep track of just where I am, and often reminds me of the various options associated with a command or service. And as mentioned above, many admins are more favorably disposed towards GUI systems. This is especially true of the Windows admins who Linux advocates are interested in converting to the Light Side. While XFree86 can be configured for remote use (due to its client-server design), it is big, slow, and was not designed with security in mind.
Another problem with X is that it is not easily cross-platform. Most decent X clients for Windows are commercial software, and expensive to boot. A better way to remotely administer a Linux box through a GUI would be to use software that's installed on any Windows PC: a Web browser.
One of my fellow geeks at work recently showed me a Red Hat box on which he configured Webmin. (Thanks Tom C.) This is an open source web-based administration tool for UNIX, sponsored by Caldera and made available under the BSD license. Webmin's homepage is http://www.webmin.com. It runs on a variety of UNIX flavors, not just Linux. This allows us to have a common GUI for all of our UNIXish systems, whether they're running Linux, BSD, or whatever. Anyway, I had long wanted to try out Webmin and this finally got me to stop procrastinating. I decided to combine Webmin with Trustix and see how they worked together.
One thing I had to do first, though, was to enable a way to get
Webmin onto the Trustix box. I could have used the standard CLI ftp
client to download it directly, but I found it easier to download
Webmin onto a Windows machine and transfer it over to the Trustix
server using Samba. Since I've done some hacking with Samba, and I
want to use this PC as a fileserver for Windows clients anyway, I
created a Samba share on the machine by manually editing the
smb.conf file and adding my regular user's home
directory as a network share.
A bare bones smb.conf file that will allow this
looks like:
<begin smb.conf> #====== Global Settings ============= [global] # workgroup = NT-Domain-Name or Workgroup-Name workgroup = midearth # server string is the equivalent of the NT Description field server string = Trustix Samba Server # This option is important for security. It allows you # to restrict connections to machines which are on # your local network. The following example restricts # access to two C class networks and the "loopback" # interface. For more examples of the syntax see # the smb.conf man page hosts allow = 192.168.10.127. #======= Share Definitions ========== [homes] writable = yes comment = Home Directories browseable = no [frodo] valid users = frodo path = /home/frodo write list = frodo <end smb.conf>
I then used the smbpasswd command to sync the
passwords for my Windows, Linux, and Samba user accounts. E.g.,
root@bagend# su frodo
frodo@bagend$ smbpasswd New SMB password: (The password is not
echoed to the screen.)
Retype new SMB password:
Password changed for user frodo
frodo@bagend: exit
root@bagend#
I then started the Samba daemon (smbd), and the
directory showed up on my Win2K box in My Network Places. Starting
smbd is done with the following command:
root@bagend# /usr/sbin/smbd start
Then I used ntsysv to select smb as
one of the daemons that start automagically on boot.
Readers who need more information on Samba can go to the official website at http://www.samba.org. Also, I've found "Using Samba" from O'Reilly to be a very useful resource. In fact, the whole book is available online at http://www.oreilly.com/catalog/samba/chapter/book/index.html.
After firing up Samba, I was able to copy the Webmin tarball
over to the Linux PC and install it. (Although Webmin is available
in RPM format, I chose to get it as a UNIX tar.gz
file, since the RPMs are not specifically made for Trustix.) After
it's copied over and in the right directory (I moved it to /opt),
your untar it by:
root@bagend# tar -xvzf webmin-0.86.tar.gz
This created a directory named webmin-0.86 under /opt. You then cd to that directory and run the setup script:
root@bagend# cd webmin-0.86
root@bagend# ./setup.sh
Webmin's interface is in a word, slick. Much like the Cobalt Qube and Rebel Netwinder, it allows you to admin a Linux box through your web browser. Most system administration tasks can be performed through Webmin's default modules, and many third-party add-ons are available. The login screen you get when you first connect to the box through your browser looks like this:
In effect, Webmin allows you to take a regular PC and turn it into a "server appliance." A separate web server, like Apache, is not required, since Webmin installs its own.
By default, Webmin accepts plain HTTP connections on port 10000,
but the port can be changed, and it can be configured to work with
HTTPS so that your sessions are encrypted. I strongly
recommend this, especially if you are going to connect to your
server over the Internet. But it's good to do so even if you're
only connecting over a LAN; Insiders compromise most cracked
systems. To enable HTTPS connections, you need to install the
Net::SSLeay Perl module, which can be downloaded from
CPAN and installed from within Webmin itself.
In tune with my security concerns, you can restrict access to specific hosts and users. Further, Webmin can be configured to run in the background, waiting for connections, or setup so that you need to manually start it from the command line. Even if you have the Webmin server running, it uses far fewer system resources than the X Window System, so there's much less of an adverse performance impact.
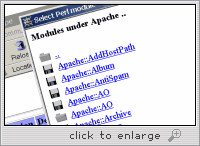
Webmin allows you to perform many common system administration
tasks, including adding and removing users and groups, configuring
NFS and NIS, monitoring disk quotas, configuring bootup and
shutdown, viewing logs, scheduling cron jobs, and even
includes a Java-based file manager and text editor. Webmin links to
these and more are visible in this screen shot:
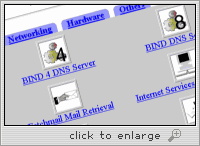
The main point of entry to the configuration pages for Apache, BIND and other daemons is the Servers tab:
As you can see, combining Trustix with Webmin allows us to create a secure server appliance that provides many needed network services, which allows secure remote administration through a GUI, and from any platform with a Web browser. This gives us a system which is ideal for small to medium sized business and managed service providers, and doesn't require Linux gurus for daily administration, although some Linux knowledge is required to get it initially set up. Kudos go to the developers of Trustix and Webmin for putting out such useful tools.
The author is a Field Systems Engineer for a broadband ISP in southeastern Pennsylvania, and was bitten by the Linux bug (penguin?) about three years ago. Before becoming a full-time geek, he was a practicing lawyer, but is feeling much better. The author has his own Linux-related Web site at www.Building-Tux.com. This is his second article for Linux.com.
Copyright (c) 2001 Dave Markowitz dave@davemarkowitz.com
![[Login Screenshot]](/img/news/inline/12472/login-thumb.gif)
![[System Screenshot]](/img/news/inline/12472/system-thumb.gif)